Cyberoam Intellegent Reporting
Enterprises require a comprehensive view of network usage and security information for zero-hour protection against emerging threats. What is critical though is reporting on the individual user activity to ensure security against the current user-targeted external threats and insider threats.
Further, security solutions are incomplete without reporting on network activity. Hence, Cyberoam offers the most comprehensive enterprise-wide and individual user identity-based reporting on its CR appliances themselves, eliminating the need to make a separate investment on a reporting solution and its integration.
When enterprises deploy Cyberoam CR appliances, they automatically have access to the unique on-appliance reporting that Cyberoam network security appliance offers in the form of real-time analytical reports that are concise and ready-to-interpret. Through this, enterprises are able to quickly summarize security threats on the network and fine-tune policies for instant preventive action, creating advanced levels of security and productivity and to meet compliance needs.
Cyberoam Dashboard
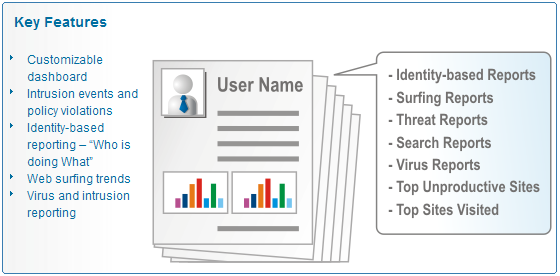
Cyberoam Dashboard provides a brief synopsis of the enterprise’s current surfing trends, bandwidth and system utilization, productive working hours, intrusion alerts and more — all on a single, customizable page. It offers enterprises the ability to identify usage and threat patterns and potential areas of risk and productivity loss, enabling them to understand, plan and fine-tune their security strategy. With Cyberoam Dashboard, enterprises get fast access to monitor and analyze employee Internet usage, enabling them to control data and applications that employees use during their working hours.
On Appliance Intelligent Reporting – Cyberoam iView
Cyberoam, integrated with Cyberoam-iView offers a wide spectrum of more than 1000 unique user identity-based report templates across applications and helps organizations monitor their networks across multiple devices for high levels of security, data confidentiality while meeting the requirements of regulatory compliance.
Cyberoam-iView provides a complete view of enterprise security posture and rapidly identifies suspicious patterns of activity that would otherwise go unnoticed, on a single screen. Organizations receive detailed drill-down reports through iView with a clear view of users and their activities over any device and location.
Enterprises also have the flexibility to customize formats for report viewing. Reports can be viewed in tabular, graphical and printer-friendly formats, and can be exported in CSV and PDF format for further data analysis.
User Identity-Based Reports – Enabling Regulatory Compliance
User identity-based reporting plays a critical role in meeting regulatory compliance and audit requirements. By taking the user identity beyond authentication into the network, Cyberoam offers a range of identity-based reports, including broad overview as well as drill down information related to user activity and threat incidence, ensuring regulatory compliance and short audit cycles.
With identity-based reports related to Internet and application access as well as source or destination with the username, Cyberoam enables enterprises to zero-in on compromising activity and users instantly even in DHCP, Wi-Fi and desktop sharing environments like healthcare, educational institutions, retail stores, call centers and more. This enables enterprises to identify pattern changes in usage by the user and enables fine-tuning user access policies accordingly, supporting advanced levels of security and productivity.
Network and Application Monitoring
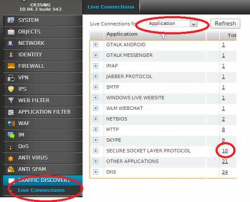
Cyberoam’s Traffic Discovery offers information on current traffic movement, alerting administrators to unproductive usage and threat incidence as they happen. Enterprises can control usage of file-sharing applications like IM and P2P based on user’s data transfer details. They can take instant action by isolating threat generating systems, controlling activity from compromised devices and access to users who are choking bandwidth with indiscriminate surfing and allocating committed bandwidth to critical applications and users.
Cyberoam Central Console
Cyberoam Central Console offers instant enterprise-wide security visibility. Its web-based GUI enables remote management of all distributed Cyberoam security devices, allowing instant action through real-time enforcement of security and firewall policies to control an attack and for intrusion prevention.