Configure Cyberoam with Active directory Server - Part 1
This is Part 1 of Cyberoam Active Directory Integration - Part 2 coming soon
This document outlines the steps to:
- Configure AD integration on Cyberoam (External Authentication)
- Determine FQDN, Netbios Name, LDAP DN
- Test AD Authentication
- Install Transparent Authentication (CTAS agent) on AD Server SSO (Single Sign On)
- Loose Integration vs Tight Integration
- Import Active Directory groups (optional)
Prerequisites:
- NetBIOS Domain name
- FQDN Domain name
- Search LDAP DN
If your domain was "cyberoam.local" then you Search DN will be "dc=cyberoam,dc=local" (without quotes)
If your domain was "cyberoam.com.au" then you Search DN will be "dc=cyberoam,dc=com,dc=loca" (without quotes)
Active Directory Server IP address
Username and Password (Active Directory permissions - usually administrator)
IP address of Cyberoam Interface
Step 1 - Configure Cyberoam Active Directory on the Cyberoam UTM
- Login to the Cyberoam GUI
- Go to IDENTIY—AUTHENTICATION – Authentication Server
- Click ADD
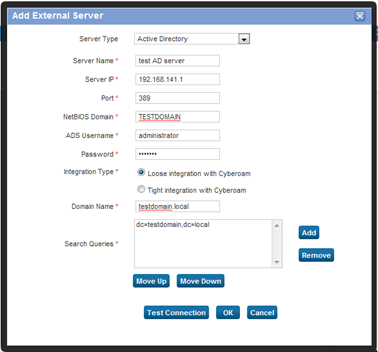
Server Type: Active Directory Server Name: <choose anyname> AD Server IP: 192.168.141.1 Port: 389 NetBIOS Domain: TESTDOMAIN ADS username: administrator Password ********* Integration Type: Tight Domain Name: testdomain.local Search Queries: dc=testdomain,dc=local - Click “TEST CONNECTION” it should say success.
- Click "OK"
Step 2 - Set AD sevrer as a method of Firewall Authentication
1. Enable AD server as a method of firewall authentication
Go to IDENTITY->AUTHENTICATION->Firewall
Under authentication methods
Add the AD server as a method of authentication.
Click “Apply”
2. Change the Simultaneous Logins to "unlimited"
Step 3 - Test the Integration
- The Test
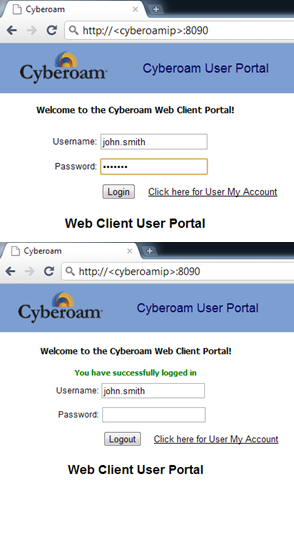
Browse to the captive Portal Page http://<cyberoamip>:8090
Login using an Active Directory username and password
You should see a message “You have successfully logged in” See screenshot - Confirm by checking logs
Go to LOGS & REPORTS-LOGVIEWER
Choose Authentication Logs
You should see a successful event for Firewall Authentication
Step 4 - importing Groups
Go to IDENTITY->AUTHENTICATION->Authentication Server
Click Import icon on the right hand side
![]()
See Part 2 here